Single Sign-On
This article is compatible with FeatBit 3.0.0 and above.
The Single-Sign-On capability is only available for customers on the Enterprise subscription. Check out the FeatBit plans (opens in a new tab) for details. You can also try this feature with a trial license, the trial license can be generated here Featbit dashboard (opens in a new tab).
SSO is available on FeatBit(an open source feature flags (opens in a new tab) service) Self-hosted via OpenID Connect. To enable SSO on your self-hosted FeatBit instance, you will need an active license key, and then you may add the SSO settings for your provider.
SSO Settings
To enable SSO, you will need to add the following settings
Add environment variable for the FeatBit Api service
SSOEnabled: Set totrueto enable SSO.
Add OpenId Connect settings via UI
Once FeatBit successfully launched, go to the UI http://localhost:8081/workspace (opens in a new tab) and add the following settings:
clientId: The OIDC client ID.clientSecret: The OIDC client secret.redirectUri: The OIDC redirect URI.tokenEndpoint: The OIDC token endpoint.clientAuthenticationMethod: The OIDC client authentication method. Set toclient_secret_postfor most of the time, we also supportclient_secret_basic.authorizationEndpoint: The OIDC authorization endpoint.scope: The OIDC scopes to request. Set toopenid profile emailfor most of the time.userEmailClaim: The OIDC user email claim. Set toemailif you use the above scope.
Example
We have tested FeatBit SSO with Keycloak, Okta, and Auth0. Here's a step-by-step guide using Keycloak as an example.
1. Run Keycloak
Run keycloak from docker and log in the admin console with admin/admin at localhost:9000 (opens in a new tab)
docker run -d -p 9000:8080 -e KEYCLOAK_ADMIN=admin -e KEYCLOAK_ADMIN_PASSWORD=admin --name=keycloak quay.io/keycloak/keycloak:22.0.1 start-dev2. Create a realm
Create a new realm called featbit and switch to that realm
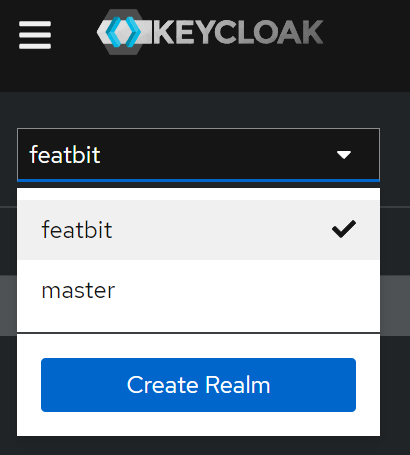
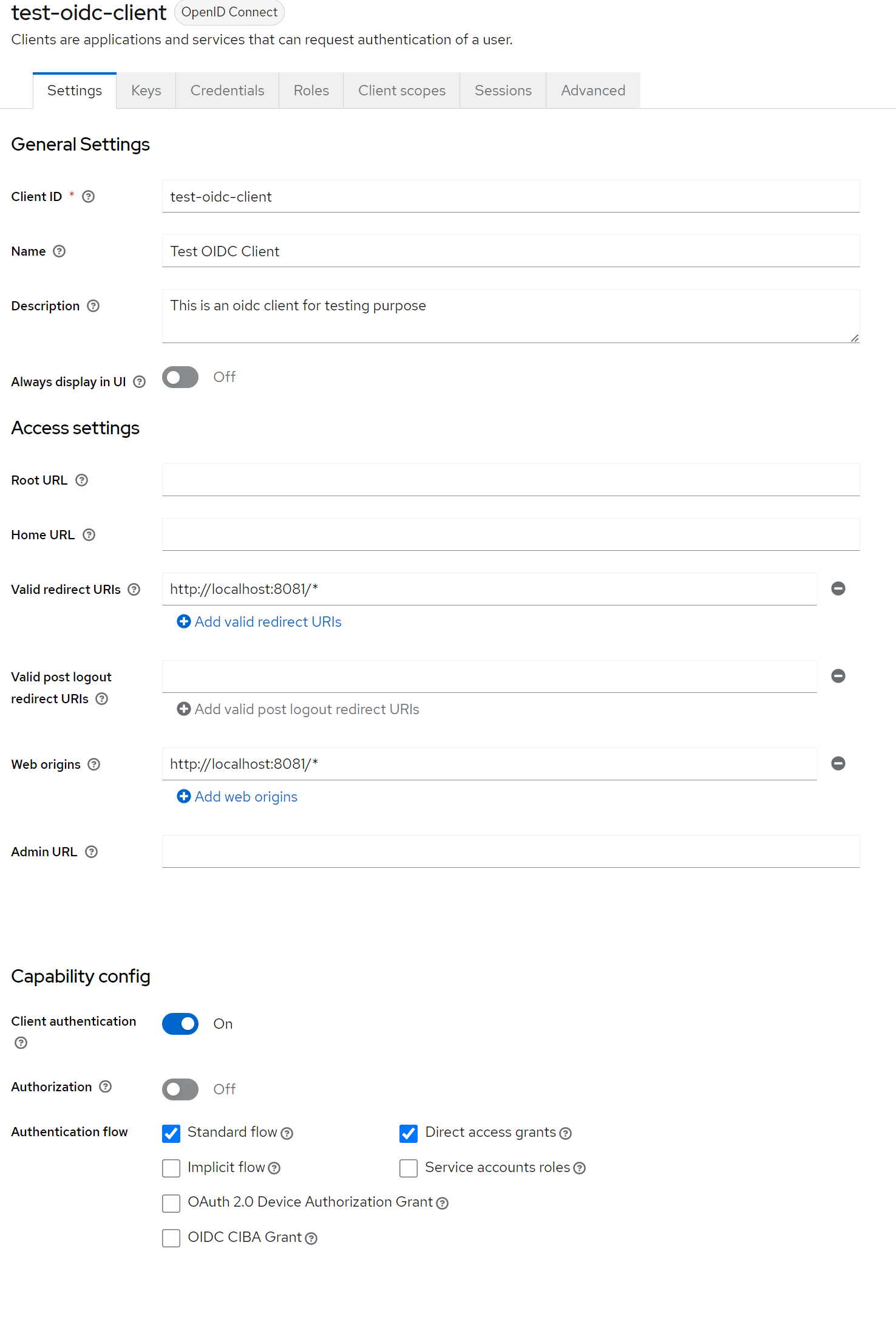
3. Create an OIDC Client
Create an OIDC client with these settings, here are some important settings:
- Set the client's Valid Redirect URIs to http://localhost:8081/ (opens in a new tab)* (FeatBit UI service address)
- Set the client's Web Origins to http://localhost:8081/ (opens in a new tab)* (FeatBit UI service address)
- Enable Client authentication
4. Create a User
Create a user on KeyCloak and set a password for that user
5. Start FeatBit
Setting the following environment variables for FeatBit Api Service in docker-compose.yml.
SSOEnabled=trueStart FeatBit and you should be able to see the SSO tab on the login page.
cd featbit
docker-compose up -d
Then click the Login tab and log in with the default credentials test@featbit.com/123456
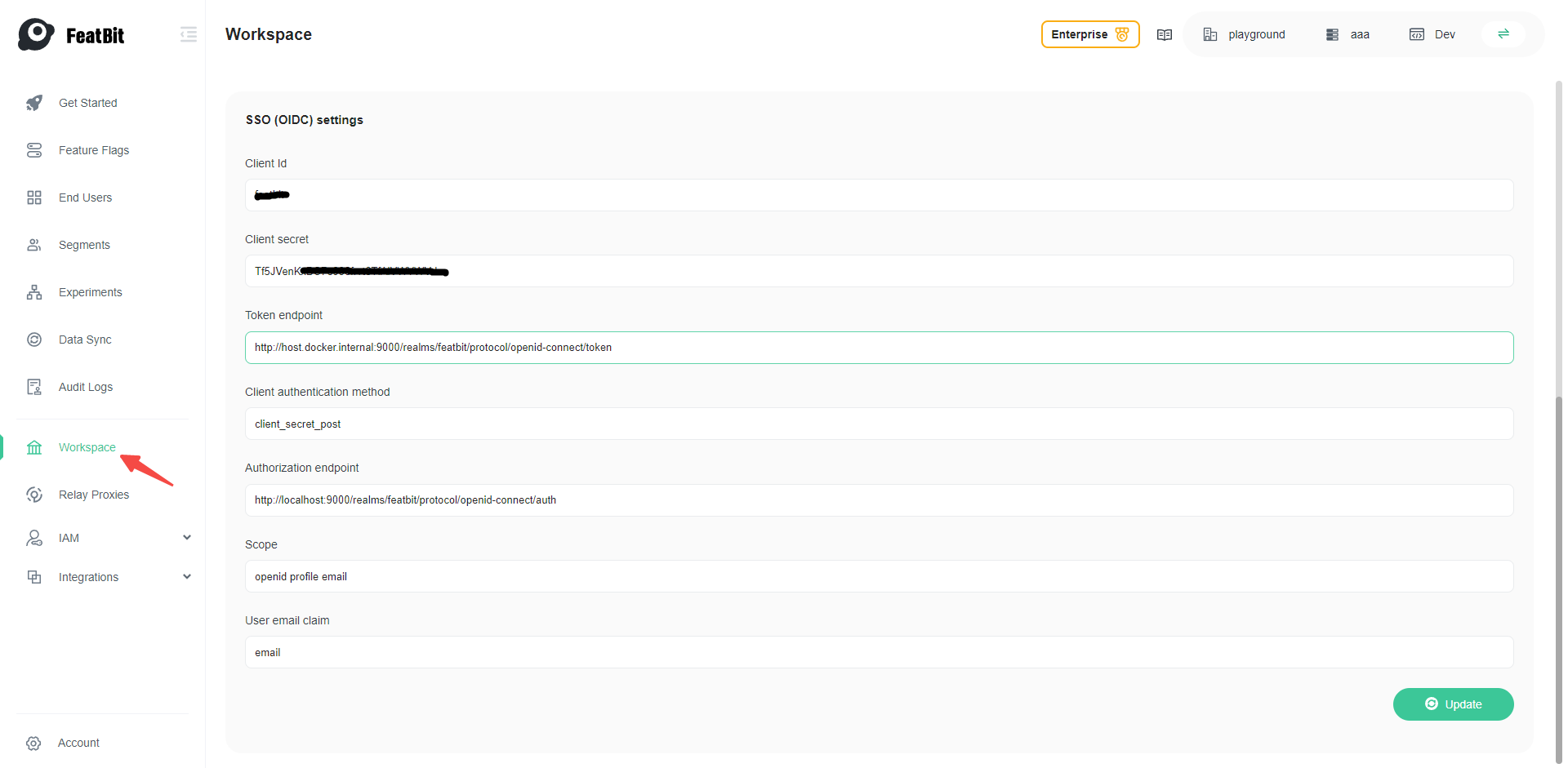
6. Configure OIDC Settings
Go to http://localhost:8081/workspace (opens in a new tab) and add your OpenID Connect settings and click on Update, please replace the client secret with your own value
7. Log In with SSO
Copy the workspace key in the General settings, you will need it when login with SSO
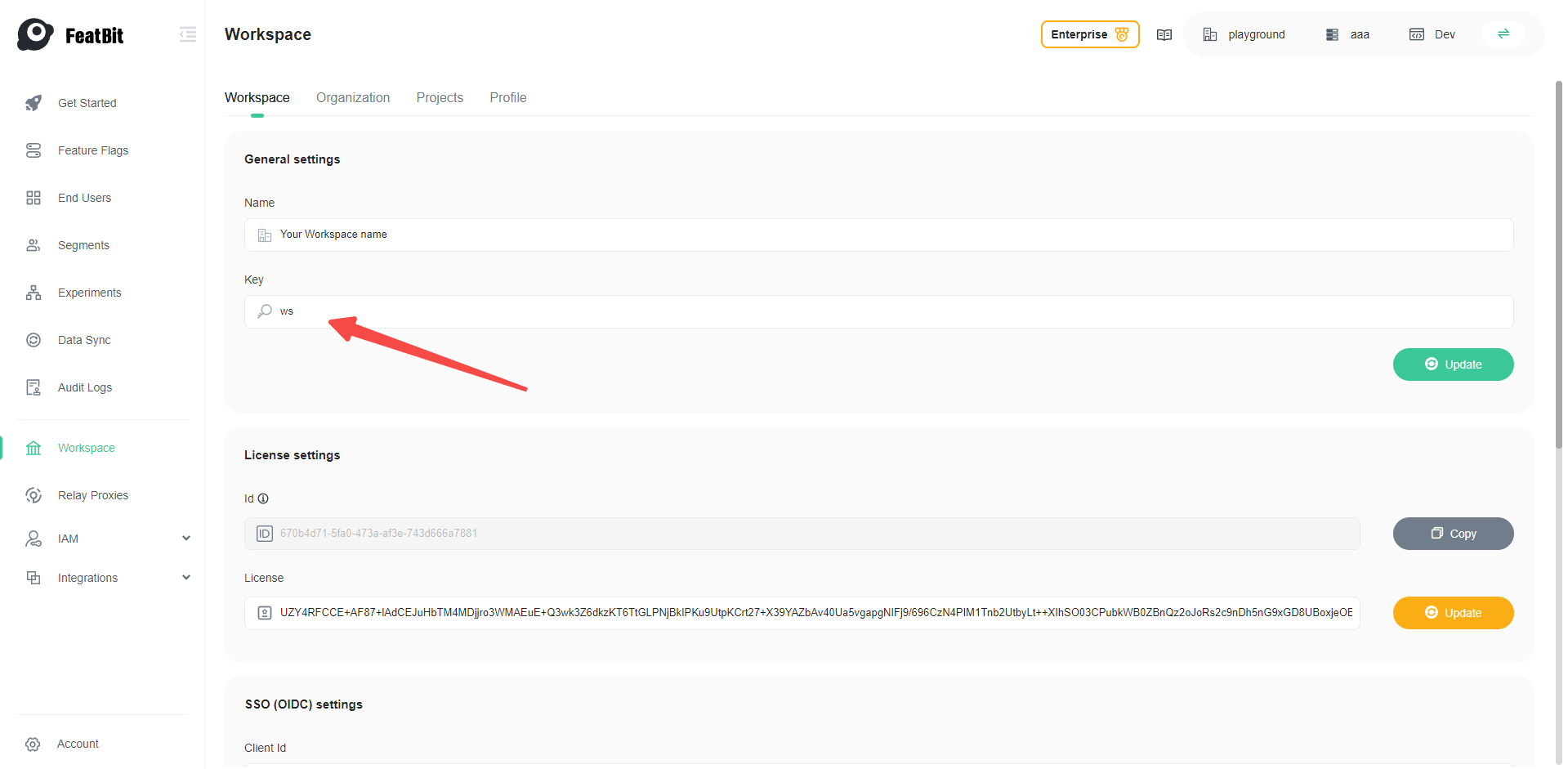
Log out and click SSO, use the workspace key copied earlier. Click Continue and the browser should take you to the Keycloak login page, then you can log in with the user you created previously.